Network Security Group Max Rules
Security groups per network interface.
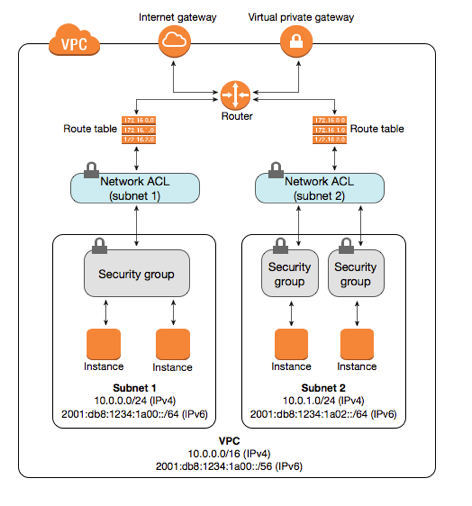
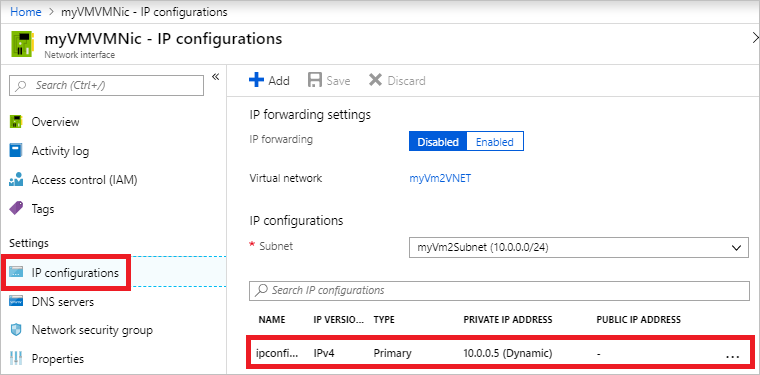
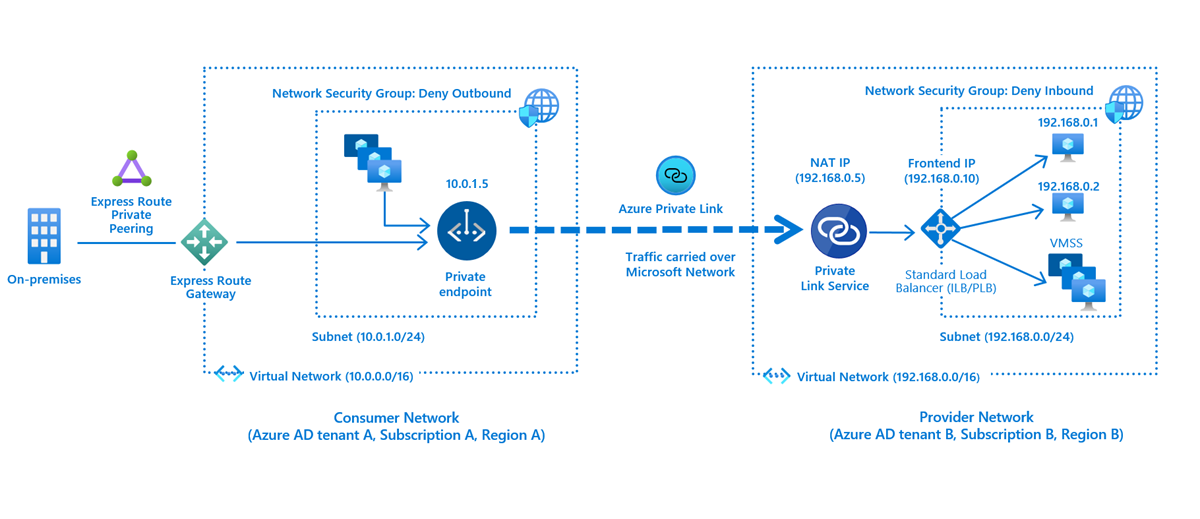
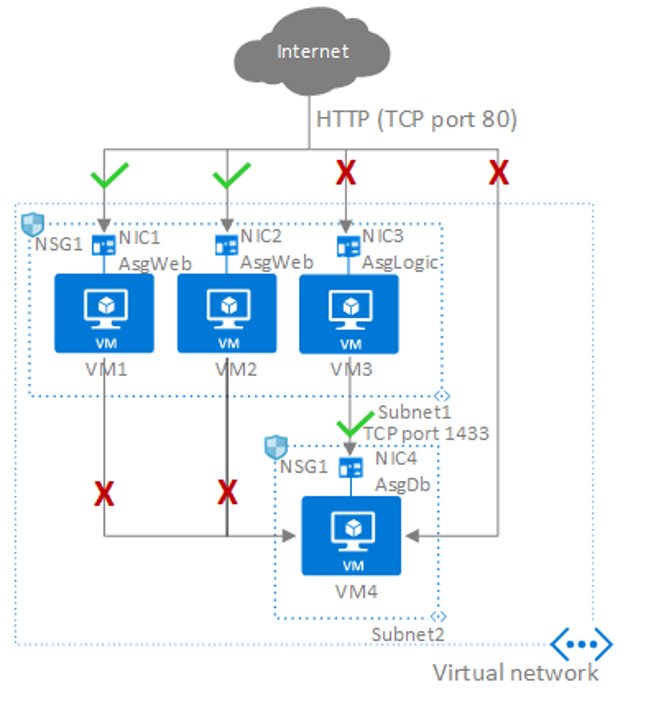
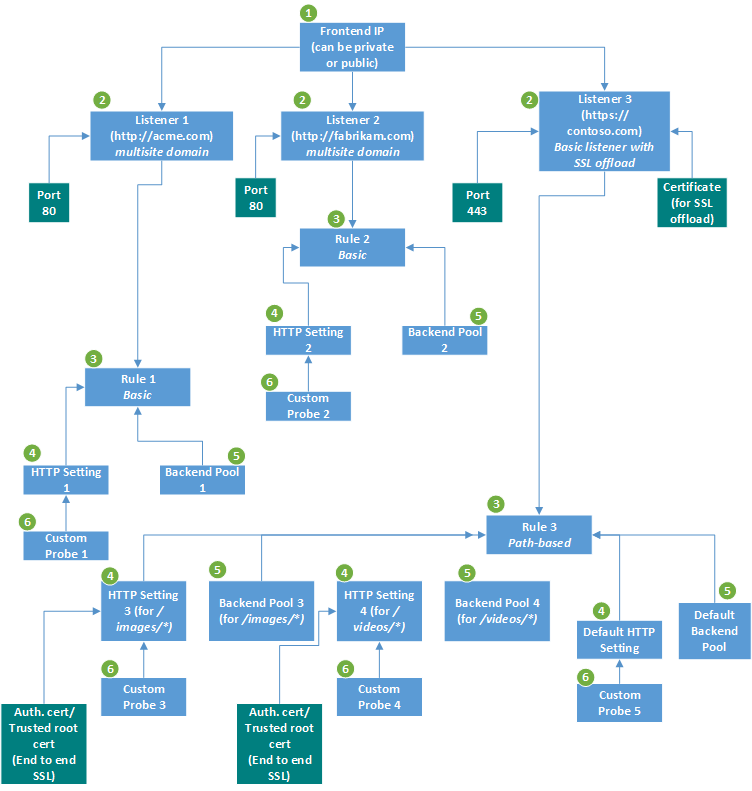
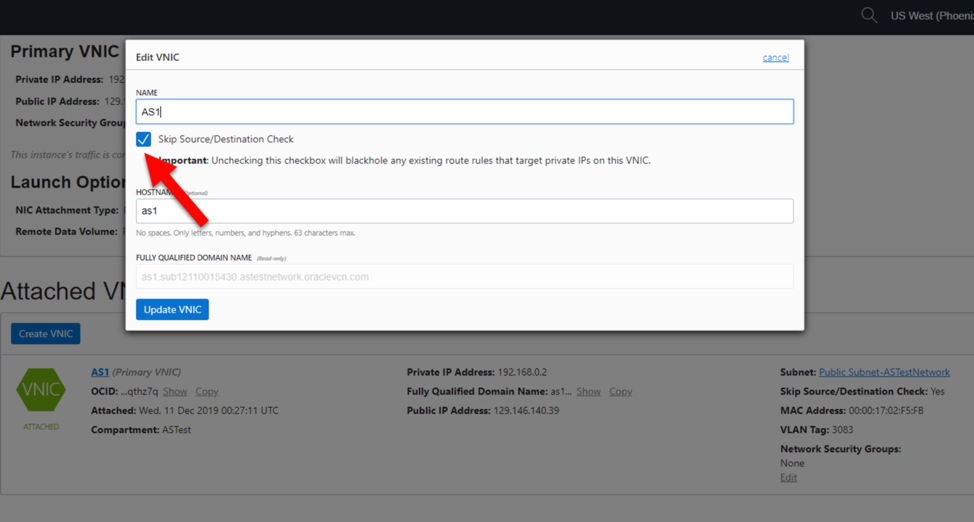
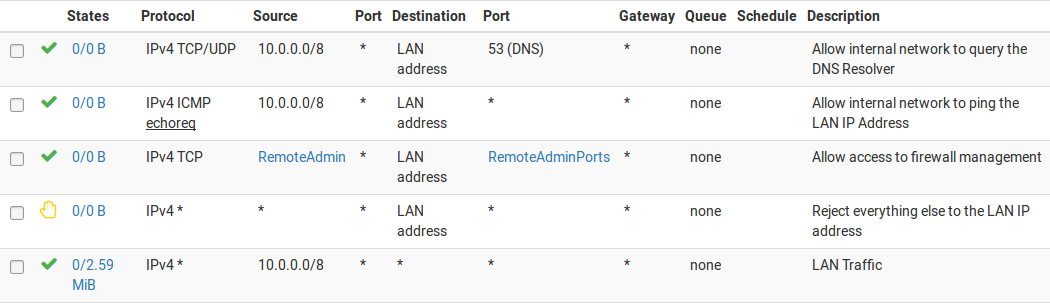
Network security group max rules. The default rules in a network security group allow for outbound access and inbound access is denied by default. After you launch an instance you can change the security groups that are associated with the instance which changes the security groups associated with the primary network interface eth0. Network security groups strives to provide granular access control over network traffic for services running in the vnet and aligning with that goal a subscription is allowed to have up to 100 network security groups with each network security group having as many as 200 rules. All the compute instances that act as web servers in the web tier of a multi tier application in your vcn.
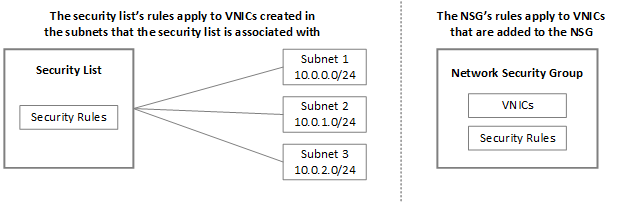
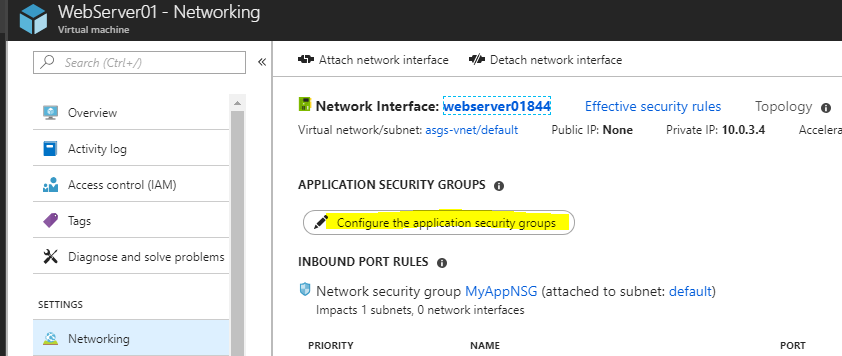
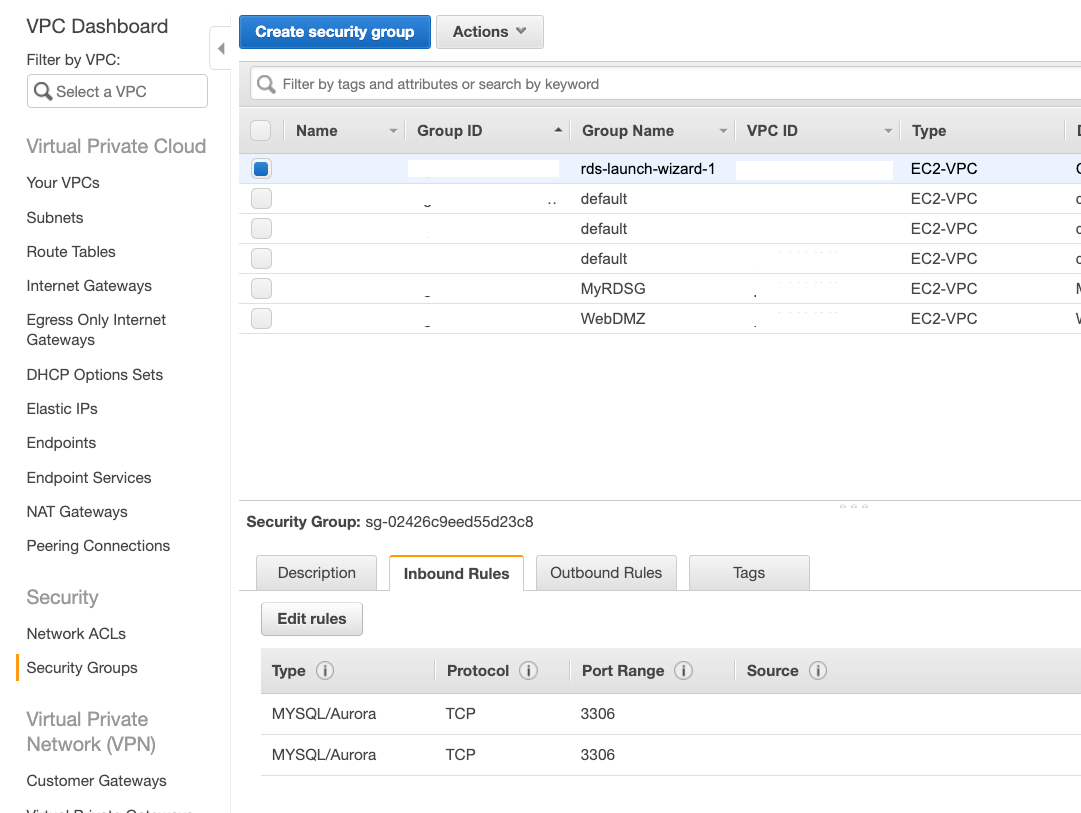
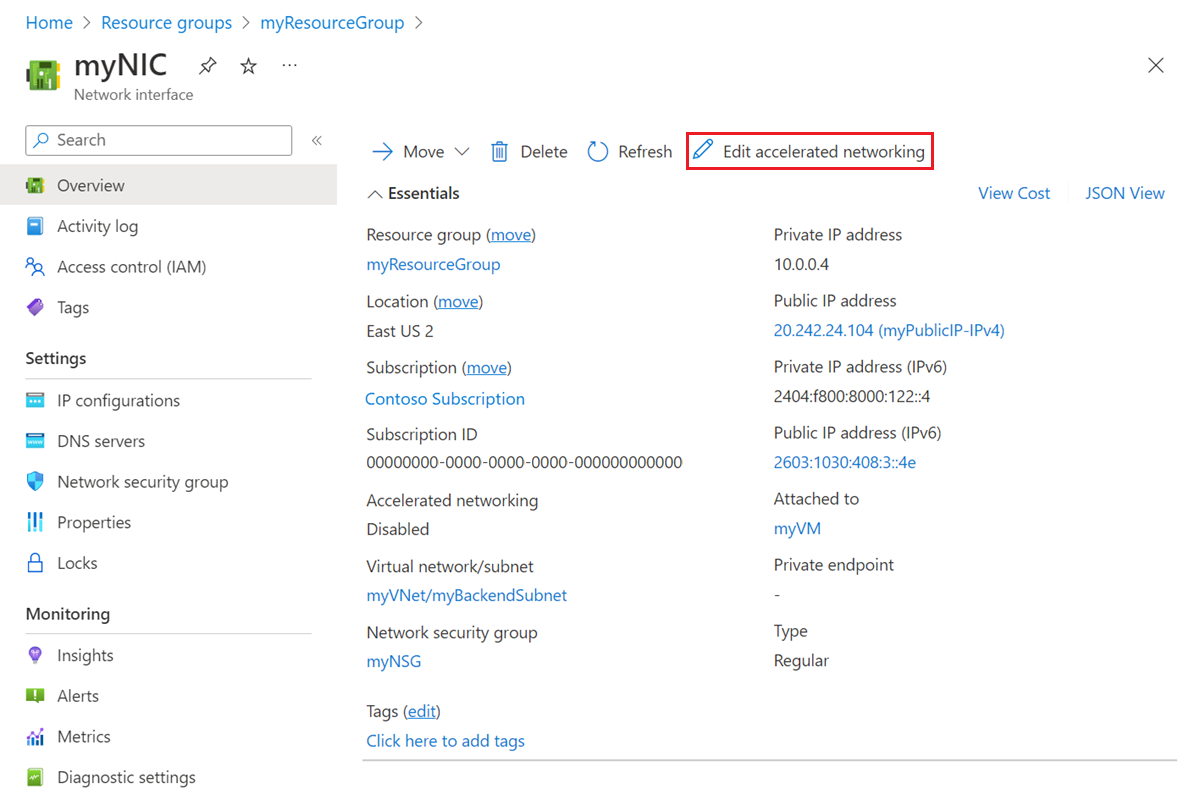
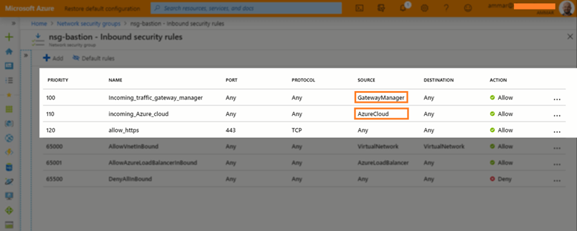
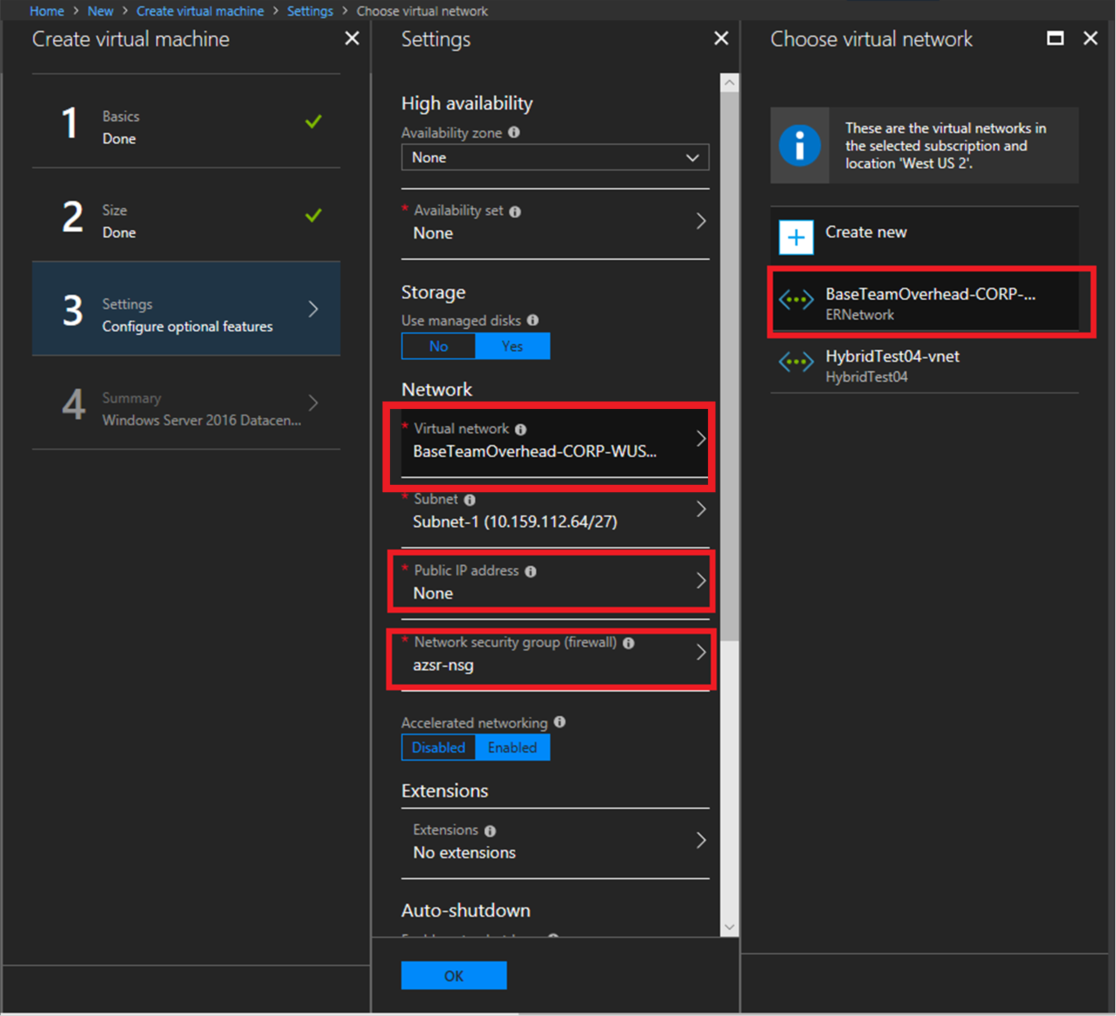
Security groups are associated with network interfaces. For an example of security group rules for web servers and database servers see security. Network security groups nsgs act as a virtual firewall for your compute instances and other kinds of resources an nsg consists of a set of ingress and egress security rules that apply only to a set of vnics of your choice in a single vcn for example. If azure databricks needs to add a rule or change the scope of an existing rule on this list you will receive advance notice.
Nsgs can only be used in the azure region that it was created in. If you reference a customer managed prefix list in a security group rule the maximum number of entries for the prefix lists equals the same number of security group rules. Network security groups nsg are essentially traffic filters. Source and destination port ranges udp or tcp protocol can be defined maximum of 1 nsg per vm or subnet.
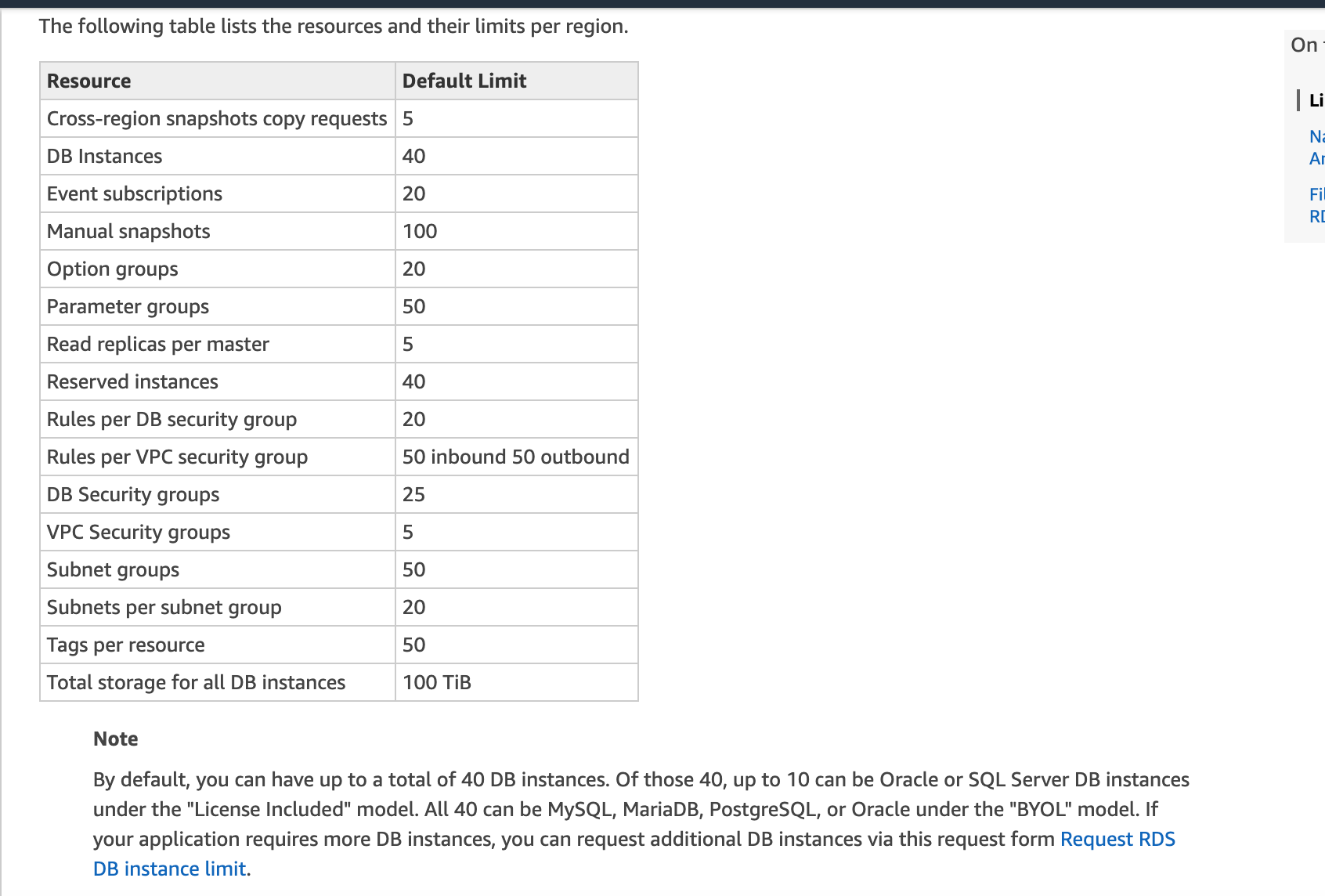
Access within the vnet is allowed by default. Like normal acls the rules are processed based on a priority. Network security group rules. How do i increase my security group rule quota in amazon vpc.
2020 09 21 i ve reached the quota for rules per security group or security groups per network interface in my amazon virtual private cloud amazon vpc. This article describes properties of a network security group rule the default security rules that are applied and the rule properties that you can modify to create an augmented security rule. Each rule specifies the. A network security group contains zero or as many rules as desired within azure subscription limits.
The maximum is 16.