Network Security Issues In Computer Networks Ppt

Top 10 best network security tools network scanning is a process of identifies the active hosts clients and servers on a network and their activities to attack a network and protect from vulnerabilities and hackers.
Network security issues in computer networks ppt. Network channels and components may be unreliable resulting in loss of bits while data transfer. Examine and monitor log files preparing your system for an attack is only part of the battle. When businesses connect their systems and computers one user s problems may affect everyone on the network. We ve covered the history of web exploiting and the biggest exploits the world has experienced but today we re going back to basics exploring and explaining the most common network security threats you may encounter while online.
A number of design issues exist for the layer to layer approach of computer networks. A well rounded education in cyber and network security can expose you to many common methods hackers use to gain access to networks and give you the hands on training you need to think beyond simple security methods and prevent even a highly technical well organized cyber criminal from getting in. It becomes complex when you are working in a large organization where hundreds of networks are connected. All of these network problems increase in size according to the size of the network.
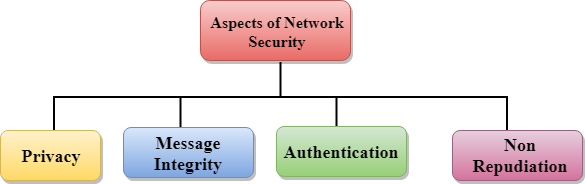
Network security is the security provided to a network from unauthorized access and risks. System security running security audits design a routine or make use of tools that will scan computer systems for bad configuration files altered programs and other potential security problems on a regular basis. Computer networks that are involved in regular transactions and communication. Computer networking network security issues.
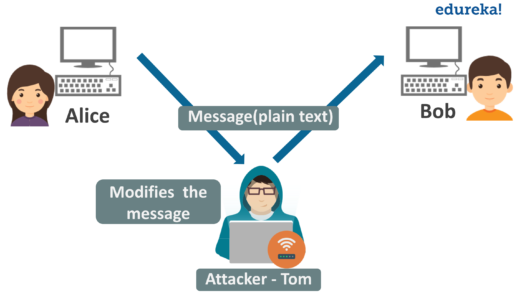
So an important design issue is to make sure that the information transferred is not distorted. Some of the main design issues are as follows reliability. One of the most important issues in any computer network is the security issues which generally involve protecting the network from denial of service attacks dosa preventing unauthorized users to infiltrate the system and maintaining network integrity. We ve all heard about them and we all have our fears.
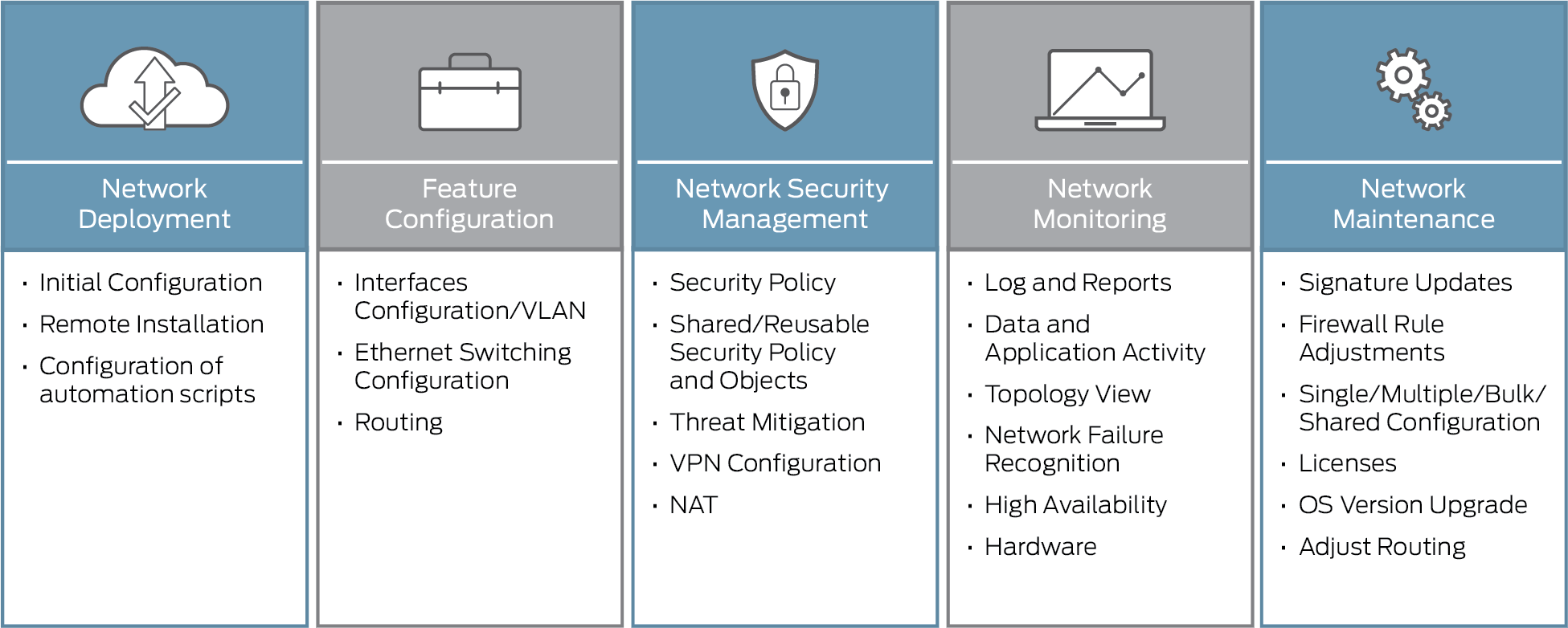
It is the duty of network administrators to adopt preventive measures to protect their networks from potential security threats. Despite the many benefits of using networks networking raises a greater potential for security issues such as. To start a computer network business you know the basic requirement you need like switches routers and ethernet cable port. Here derek gentry shared some tips on ppt about small business computer network setup.
Derek gentry says computer network business is a good way to connect to the web. So every network administrator looking for the best network security. The main purpose of the networks is to facilitate communication through video.