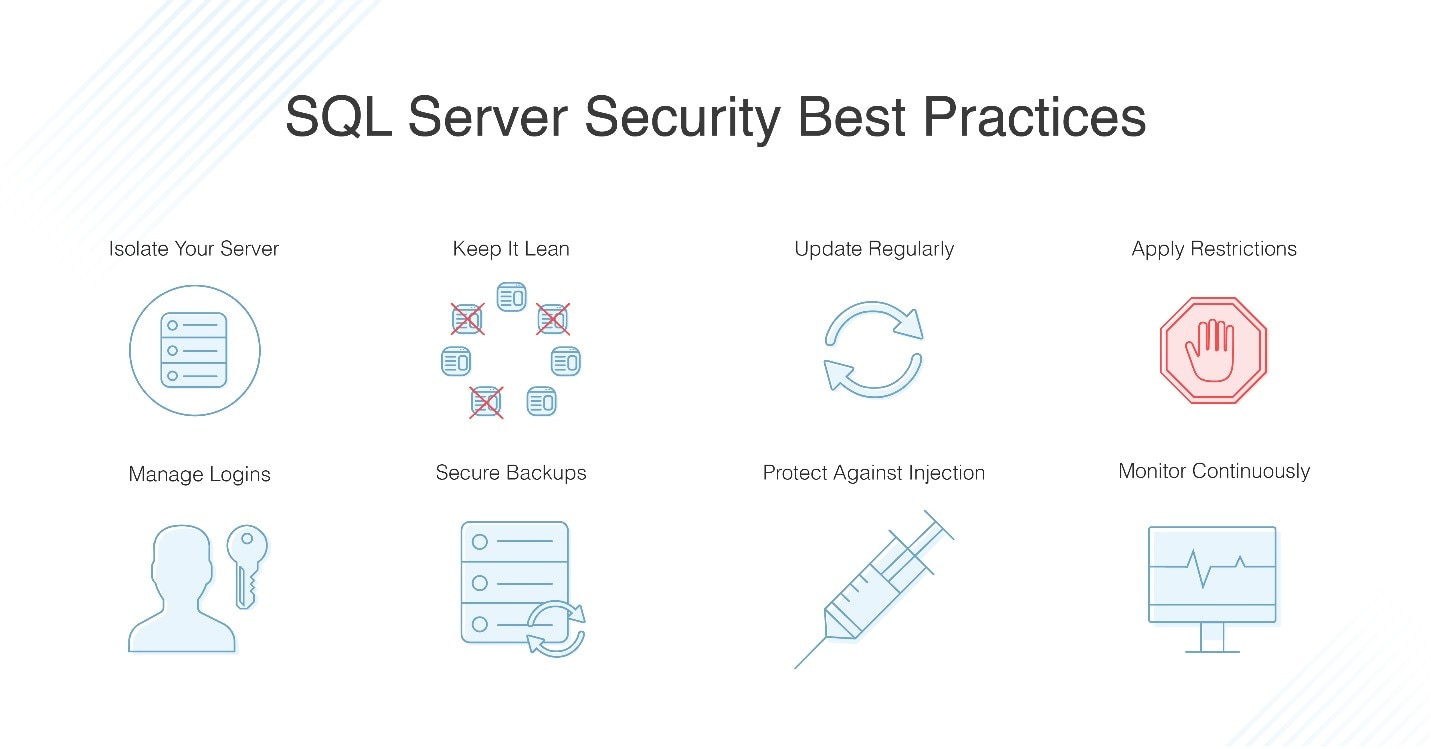
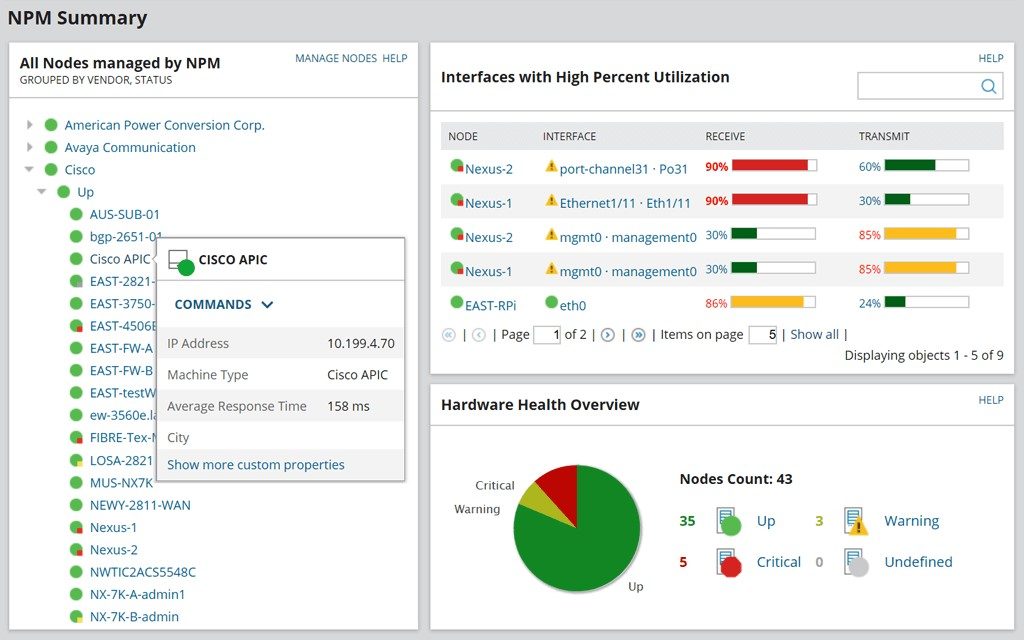
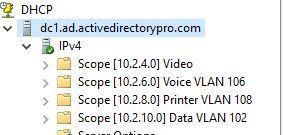
Network Segment Best Practices
By default there are no network access controls.
Network segment best practices. The purpose is to improve network performance and security. 1 protect your endpoints. Network segmentation is a best practice that can help to reduce the damage caused by a malware or ransomware attack. Segmentation divides a computer network into smaller parts.
One cybersecurity mechanism stood out as very effective in limiting the damage in case of a network breach. Network segmentation is vital in order to limit the risks for business data after a network intrusion. Segment the larger address space into subnets. October 23 2016 network security.
The other way they gain entry is after compromising an endpoint and stealing credentials for network segments. The framework is composed of the following components. The proposed framework starts by logically breaking up the network infrastructure and placing the business critical resource at the center of the architecture the business critical resource could be anything you want to protect from unauthorized users or objects. Network segmentation projects are on everyone s radar for 2019.
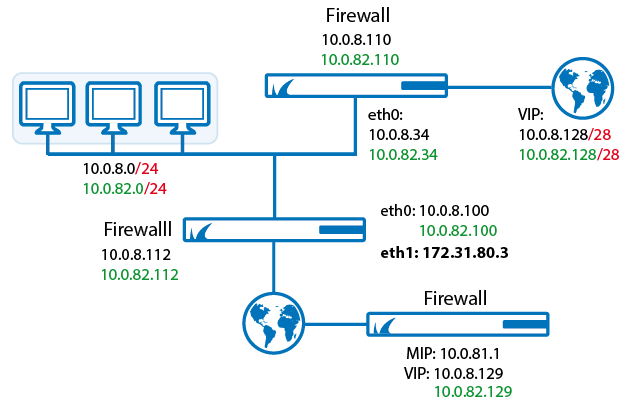
When a network is too heavily segmented it can be harder to manage and even affect the network s performance which impacts. A network breach is an inevitable risk online. Network segmentation best practice 1. Use cidr based subnetting principles to create your subnets.
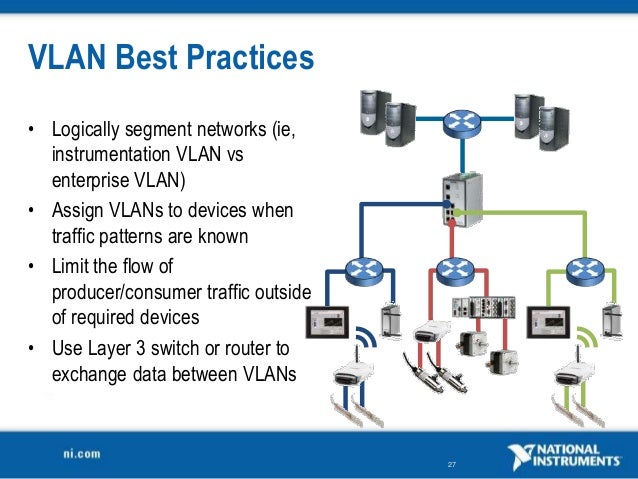
Best practices for network segmentation. Cyber criminals access the network through network endpoints. Create network access controls between subnets. With network segmentation lateral movement is much harder so it is easy to contain malware and limit file.
To help you experience the benefits of network segmentation here are a few network segmentation best practices to get you started. Routing between subnets happens automatically and you don t need to manually configure routing tables. Other terms that often mean the same thing are network segregation network partitioning and network isolation. Attacks are bound to occur and every network must be able to withstand a break in.
7 network segmentation security best practices. If a computer is compromised attackers will attempt to more laterally and access other devices and parts of the network. The goal is to make very difficult the movement of threat inside the network and to give to intruders not authorized the minimun privilege possible for avoiding the. Network segmentation best practices.
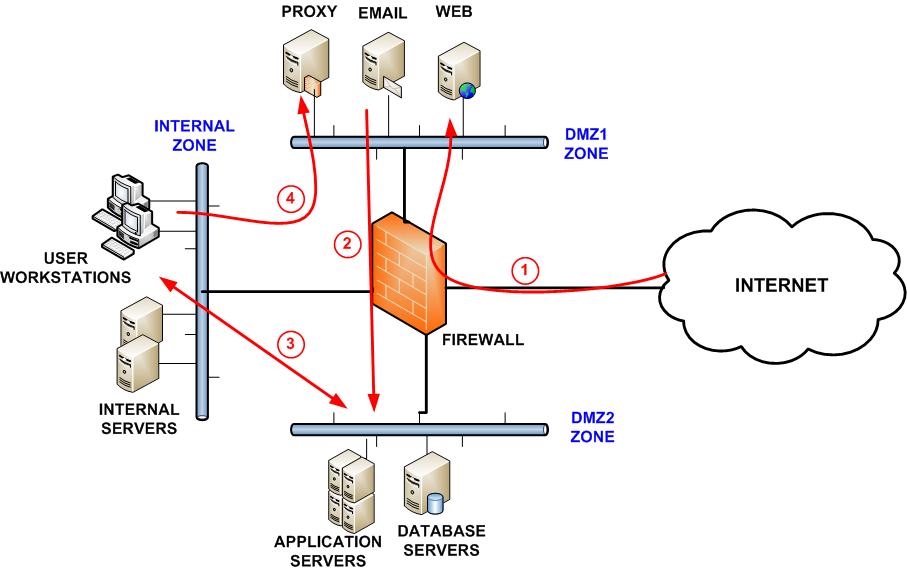
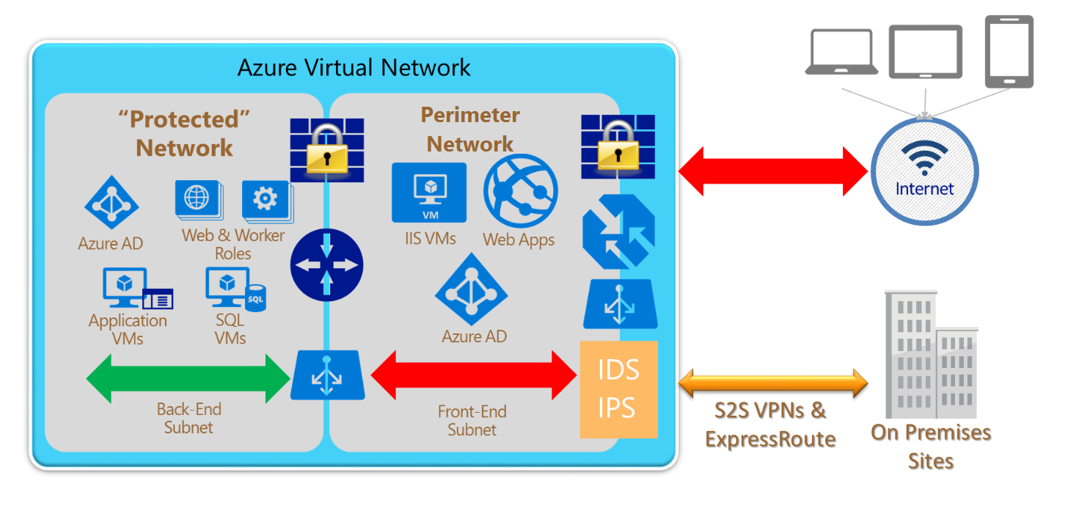
For one thing it is essential that your design features an internal zone that is highly protected against breach and never directly accesses the internet. A strong network security structure should contain several parts. Be cautious of over segmentation. It is a best.