Network Segmentation Best Practices Nist
Network segmentation network path redundancy firewall.
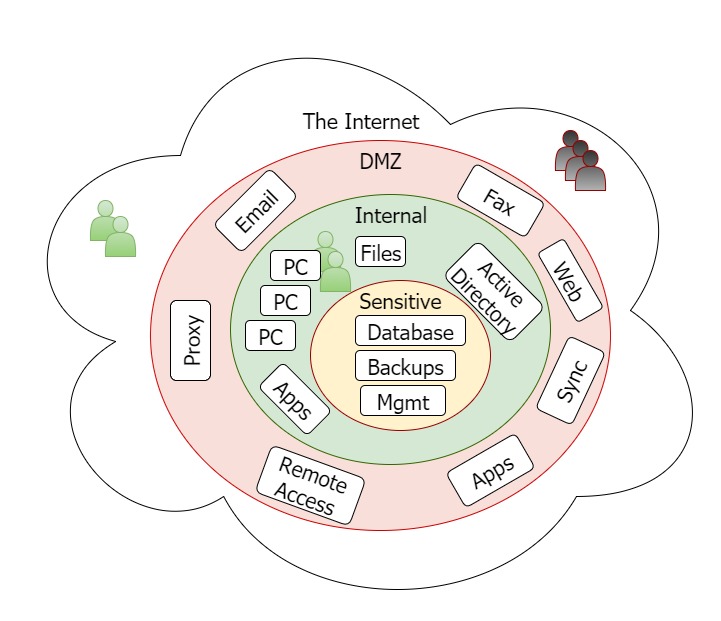
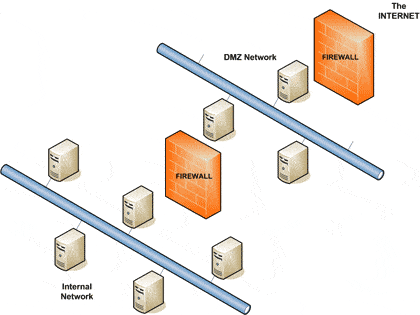
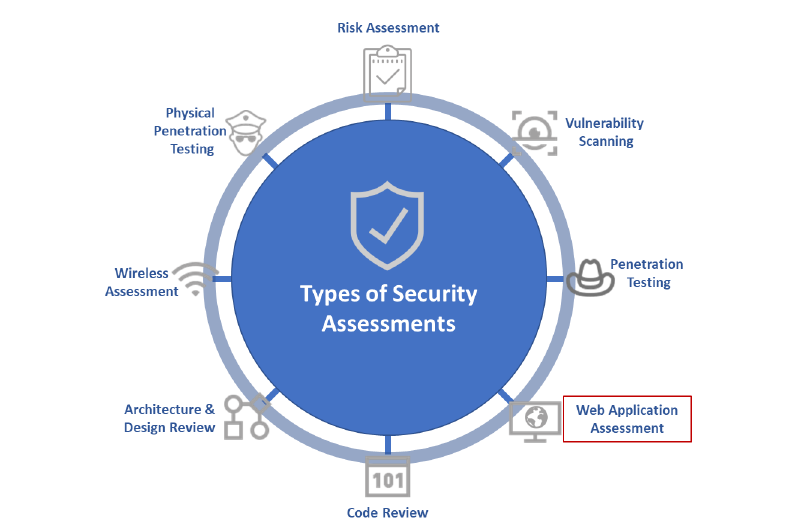
Network segmentation best practices nist. Network segmentation projects are on everyone s radar for 2019. Nist requests public comments on draft special publication 800 125b. Network segmentation best practices a strong network security structure should contain several parts. Network segmentation makes it more difficult for an attacker to perpetrate an attack throughout your entire network.
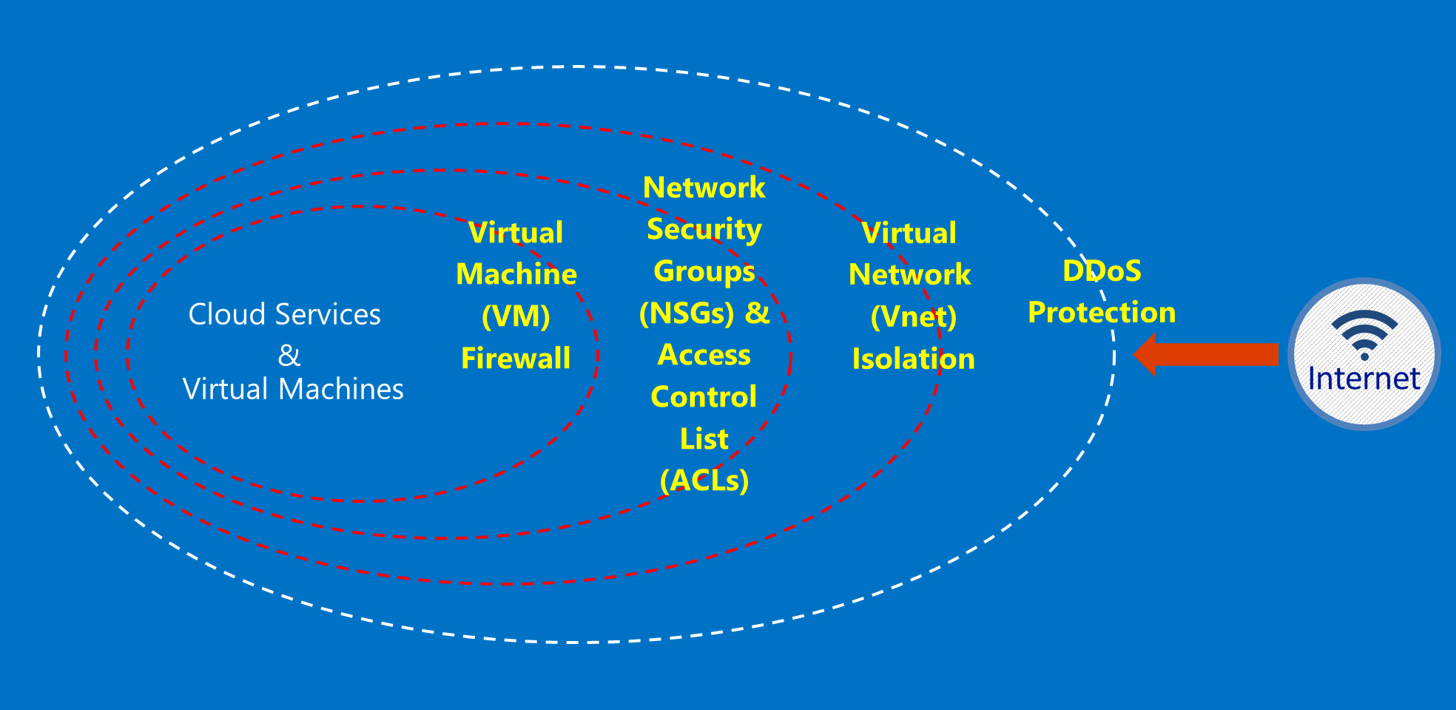
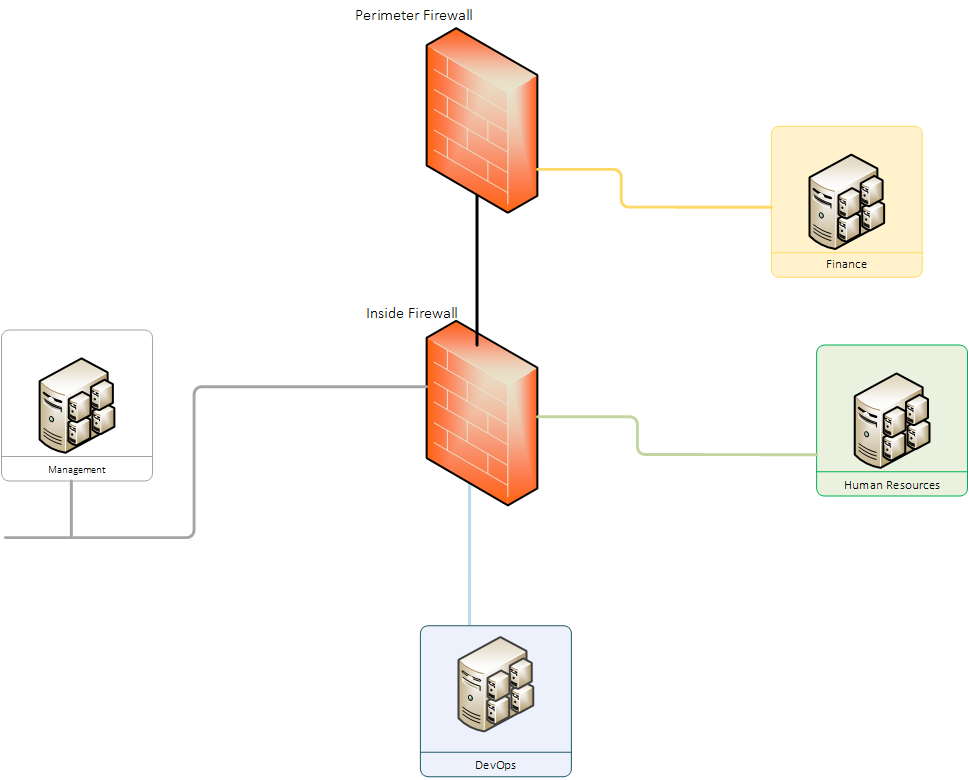
8 nist cybersecurity framework a widely used risk based approach to managing cybersecurity composed of three parts. Secure virtual network configuration. Network segmentation minimizes the harm of malware and other threats by isolating it to a limited part of the network. Since vms are end nodes of a virtual network the configuration of the virtual network is an important element in the security of the vms and their hosted applications.
Virtual machines vms are key resources to be protected since they are the compute engines hosting mission critical applications. The segmentation of the network using the concept of virtual lans segmentation at the layer 2 l2 or data link layer and its advantages and weaknesses are the topic of section iv. From a regulations and best practice standpoint network segmentation is starting to be more prevalent. The framework is composed of the following components.
Nist special publication 800 125b. For one thing it is essential that your design features an internal zone that is highly protected against breach and never directly accesses the internet. Or equipment are necessarily the best. There may be references in this publication to other publications currently under development by nist in.
Or equipment are necessarily the best available for the purpose. The proposed framework starts by logically breaking up the network infrastructure and placing the business critical resource at the center of the architecture the business critical resource could be anything you want to protect from unauthorized users or objects. The virtual network configuration areas discussed in this document are network segmentation. These projects are a massive undertaking that can drastically improve the security of an organization but they also touch every part of the business and introduce considerable risks.
It s also an obstacle for insiders because you can isolate sensitive data and systems from curious insiders. Virtual network configuration areas discussed in this document are network segmentation. Available for the purpose.