Network Segmentation Security Best Practices

One cybersecurity mechanism stood out as very effective in limiting the damage in case of a network breach.
Network segmentation security best practices. Otherwise you run the risk of missing some endpoints and connections on the network creating security gaps that an attacker. Conduct regular network audits. October 23 2016 network security. 7 network segmentation security best practices.
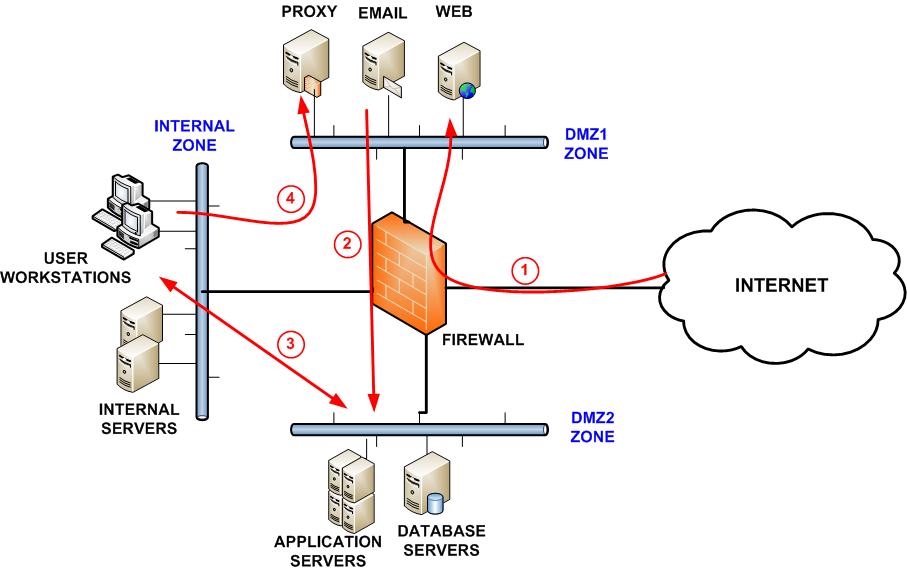
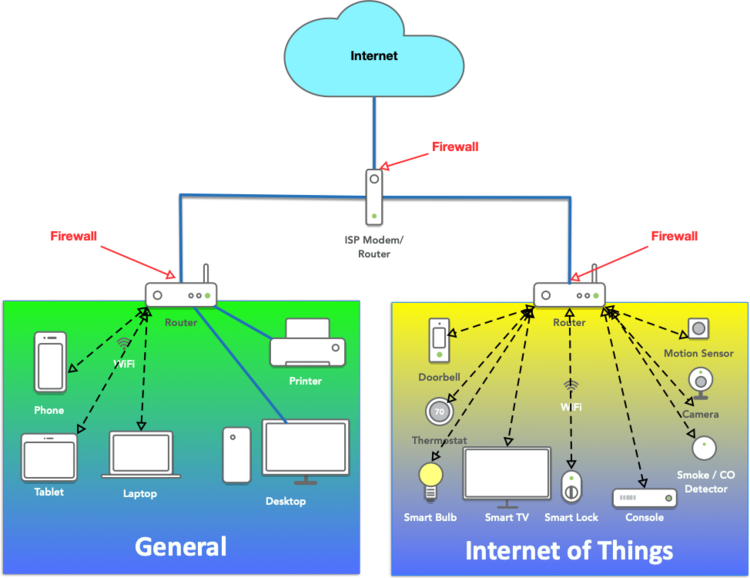
Implementing better network segmentation to improve security is a significant project for network operations data center ops and security teams. Network segmentation best practices a strong network security structure should contain several parts. In this article network segmentation best practices to create secured enterprise environment senior network engineer samuel oppong discusses the reasons why network segmentation as a concept should be employed and implemented by enterprises in the new decade. From dividing iot from it using microsegmentation to avoiding oversegmentation we call out best practices for maximizing success in this task.
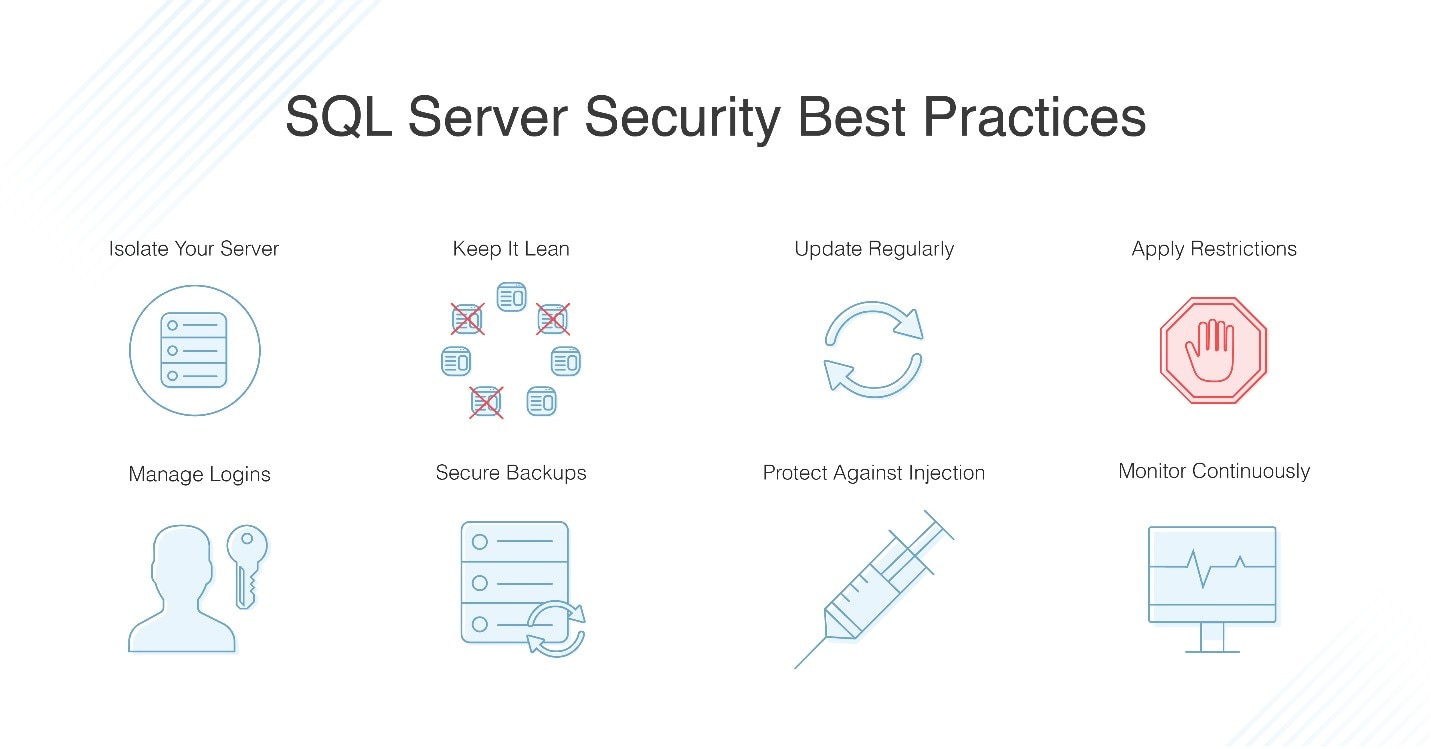
For one thing it is essential that your design features an internal zone that is highly protected against breach and never directly accesses the internet. Attacks are bound to occur and every network must be able to withstand a break in. Network segmentation projects are on everyone s radar for 2019. For best security it s best practice to configure in the databases a local firewall in order to block connections from the same network.
Network segmentation best practice 2. Why network segmentation is essential to creating a secure enterprise environment. These projects are a massive undertaking that can drastically improve the security of an organization but they also touch every part of the business and introduce considerable risks. By now you ve probably seen references to network segmentation in places ranging from this column to features on network security and discussions of best practices in network monitoring but for.
A network breach is an inevitable risk online. Best practices for network segmentation. Network segmentation best practices to improve security mar 22 2018 cybersecurity advice network security web filtering regardless of the size of your business the most effective security measure to deploy to block threat actors from gaining access to your servers workstations and data is a hardware firewall.